I'm Shawn Barker, product manager at Quest software. And I'm going to demonstrate how Quest Change Auditor can detect the potential use of golden tickets in your AD environment. A golden ticket, also known as "pass the ticket," is one of a few well-published Kerberos vulnerabilities. A hacker who has performed a little recognizance and has non-privileged access to your AD environment can use a tool like Mimikatz to elevate their privileges and gain access to sensitive data.
For this example, let's assume that I'm an external actor who has managed to compromise a regular AD user's account, which has no administrative rights in your AD domain. The user I've compromised in this case is Bob. And it was an easy job, as Bob's a social media fanatic, and he uses his cat's name as his password.
I'm logged into the domain as Bob. And I can confirm that on this local machine, it recognizes me as him. Bob has no cash Kerberos tickets.
Let me attempt to connect to the root drive of one of the domain controllers. As expected, this fails. Since while Bob is a cat lover, he's no IT admin. I downloaded the Mimikatz tool, which has built-in routines for exploiting a number of known vulnerabilities. In this case, I'm going to create a golden ticket.
Essentially, all the hacker has to uncover at this point is the name of my AD domain, a SID, which could be a well-known built-in SID like administrator, and the NTLM hash for the key distribution center service account. Finally, I'll provide a display name for the user I'm impersonating. But it's going to be difficult to track with this user does since most auditing solutions will rely on the user's SID, and that may not match the username I specify here.
The previous command creates a Kerberos ticket and writes it to a file. Now I'm going to load the ticket under Bob's user context. The "who am I" command still identifies me as Bob. But looking at the cache Kerberos tickets, I now see the forged ticket that I've just created. I can see in this forged ticket that there is an excessive lifetime for the ticket.
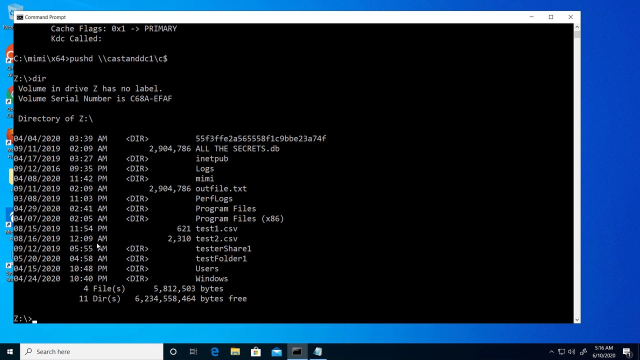
Now when I attempt to connect to the root drive of the same domain controller, the forged Kerberos ticket provides me access. Now with access to the domain controller, I can gain access to the NTDS.dit file or create backdoor accounts in AD and continue to wreak havoc.
Let me switch over to Change Auditor to show how the golden ticket I just created is detected. Change Auditor looks for Kerberos tickets with lifetimes that exceed the domain policy. The built-in logon activity reports will include these excessive lifetime ticket events, but I can also create a targeted report that only includes the Kerberos vulnerability.
Here is an example of a golden ticket being detected by Change Auditor. The event shows the username that was specified when the ticket was created and also the originating workstation. So I can track it down and determine which account was compromised in the course of the exploit. I can also turn this search into an email alert so I'll be notified right away next time a potential golden ticket is detected.
Let's take a quick look at the same events in On Demand Audit, our "software as a service" extension to Change Auditor. And I have the "out of the box" search that detects Kerberos tickets with excessive lifetimes. I can easily modify any of the parameters of this search.
And when I run the search and take a look at an event, I get a very intuitive summary of all the details of that event, again the user account that was compromised as part of this exploit and the IP address of the originating workstation. And with the click of a button, I can also turn this search into an email alert and be notified the next time this happens.
With Change Auditor for logon activity, you can promote better security, auditing, and compliance in your organization by capturing, alerting, and reporting on all user logon, logoff, and sign-in activity, both on premises and in the cloud.
 04:43
04:43
