Hello. I'm Ghazwan Khairi, a strategic systems consultant with Quest. And today I'm going to demo Quest On Demand Audit, the Azure Active Directory events.
So I've logged into my Quest On Demand. And I selected my Auditing module. And then I went to the Search section. And I selected Azure Active Directory. As you can see, we can audit events from our Office 365 workloads, as well as from our on premises Active Directory environment. For those of you who have a hybrid Active Directory environment, which will probably be you, because most of our customers have a hybrid Active Directory environment.
So on the screen here, I've got my Azure Active Directory events. There's 22 of them. These are all out of the box.
You can start clicking on these events to see the results or you can create a new search and customize the events to your liking. Maybe you're only looking for a specific parameter in an event class for your Azure Active Directory environment.
But I do want to highlight a few of these events here on the screen. So we've got Azure Active Directory failed sign-in events in the last seven days. So these are the folks that have failed to sign in into one of these targets, as you can see here on the screen. Active Administrator, Microsoft App Access Panel.
So this could be an operational I'm trying to log in and I failed, but this could also be harm that's about to hit our environment. And this allows me to take a look at it. This allows me to investigate. This allows me to create an alert and be in the know before something happens that someone is attempting to access my environment. This is one of the reports that we often get asked about.
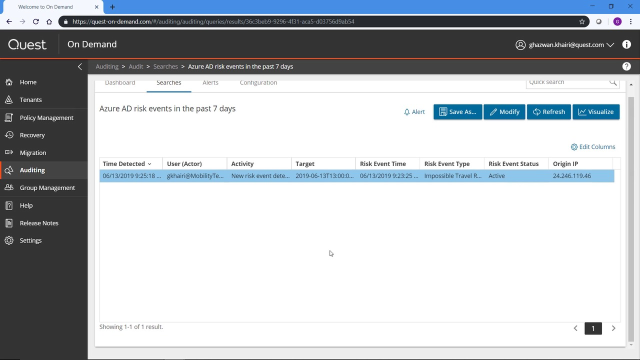
Another one in here would be risk events in the last seven days. And here I have actually generated a risk, because within a very short period of time, I had actually logged in from Ardsley, New York, and then before that, I logged in from Allen Park, Michigan. I'm not going to tell you how I did that, but you should go in and investigate how that happened, right? Like this could be a harmful-- this could be not me. This could be a user who basically hacked into my account, logged into my Azure instance, and is trying to do harm, or is trying to copy content, is trying to do things in the environment. So it's definitely something you want to be alerted against.
So if we go back to Azure Active Directory, take a look at some more of these events. One event that's really nice to kind of take a look at is the sign-in events. We're going to go ahead and visualize it, actually, rather than click the grid.
And you'll notice here, this is the visualization of the sign-ins into Active Directory. And just by looking at it from a graph standpoint, I should not be generating-- this is my account-- I should not be generating about 60% of the logins into this environment, but I am. And I did that on purpose, obviously. But this could be something that is flagged to you as someone who is looking at this, or someone who has set up an alert to be able to look at this. Why is this individual generating all these events?
So this is the overview. And you can take a look at it from a top 10 user standpoint, the activity map. This is all Active Directory single sign-ins. And then you can go by specific times. And I still keep showing up as the highest individual. So it's definitely something I need to investigate.
Look at this as I go to specific times. It looks like on June 13, I was generating 85% of the logins.
I can switch over to the sign-ins in here and take a look at the applications that these individuals-- in this case, 11 individuals-- have authenticated against. This is a list of the applications. And this is a list of the users.
I can take a look at the heat map. The applications list itself in here. If I take a look at the heat map, I can actually zoom further into this, and take a look at it. Go into Ohio. Select Ohio, right-click, and maybe you see the content of what's going on in Ohio. The city, and the-- from Powell, which is where I'm close to. And this is where it's actually generating my events.
If I go back to Azure Active Directory just so that we take a look at the rest of the events in here, we'll see information about roles, changes of roles, groups, changes of groups, changes of membership to groups. If we change tenant level information, we're going to be able to see this information in here. So a lot of helpful information about your Azure Active Directory deployment.
So that concludes this demo. For more information, visit the Quest On Demand audit URL listed on the screen.
 05:19
05:19
