I'm Shawn Barker, product manager at Quest Software. I'm going to give you an overview of how On Demand Audit proactively highlights security vulnerabilities and anomalous activity in your on-prem and Office 365 environments, as well as how it accelerates instant investigations through responsive search and interactive data visualizations.
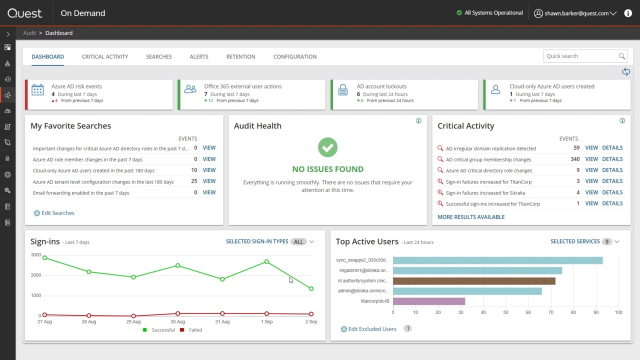
All of On Demand's AD migration and management capabilities are available through a single user portal, including Azure AD Recovery, Group Management, Office 365 License Management, and Migration. The landing page for On Demand Audit is a security-oriented dashboard that gives you a quick picture of any security alerts or trends in your environment that require your attention.
There are three sources of information that feed this dashboard-- Azure AD activity sign-ins and tenant information; Office 365 activity from Exchange Online, SharePoint, OneDrive, and Teams; and on-premises AD and authentication activity provided by Change Auditor, which is included with the On Demand Audit Hybrid Suite.
Change Auditor captures every change in activity that happens in your on-premises Microsoft environment, including changes to Active Directory, as well as authentications and logons to the Directory. Change Auditor then sends the high fidelity audit logs it has created on-premises up to On Demand Audit so that all cloud and on-premises data is available through a single, easy to use, hosted interface.
On Demand Audit's security vulnerability dashboard gives you a holistic view of all user activity across your on-premises and cloud environments, regardless of where it occurred. There are two high-level ways companies use this information. First, when something goes wrong, a detailed audit trail helps quickly determine what was changed and who changed it so that the change can be recovered. This is the reactive troubleshooting use case that On Demand Audit's customizable, built-in searches and email alerts help so well with.
Second, the security vulnerability dashboard addresses a much more proactive use case. When it comes to user activity auditing, there's so much information generated that it can be overwhelming and difficult to make sense of. 99% of that data is just innocuous user activity. The security dashboard automatically analyzes all of this activity and proactively notifies you when something suspicious has been detected so that you can investigate it further.
The widgets across the top track the trends of important activity, which could indicate that something is amiss in your environment, like a spike in risk events or an abnormally high number of account lockouts, which could be the result of a password spray attack. Green indicates a positive or neutral trend, while red would indicate a negative trend that you should investigate further.
Everything in the dashboard is actionable. Clicking on the widget or graph takes you directly to the underlying events to help speed your investigations. For example, the Office 365 external user actions widget indicates that there's been seven actions in the last seven days. If I click on the widget, I immediately see what those activities were. Each individual event tells me who, which actor, initiated the activity, what action was done, when it took place, where it happened, and if this was a change, the before and after values would be here as well.
Searches are customizable to allow you to get the information that you need. For example, I can extend this search back for weeks instead of one to see all the previous activity, and the new results are loaded instantly. Across the bottom, the sign-ins widget makes it immediately apparent if there's been a recent spike in sign-ins, which could indicate a compromised account.
A key feature of this dashboard is that every element is configurable, allowing you to filter the information to exactly what you need to be able to see. For example, I can filter out all successful logins so that I only see the failures. I can select any data point, like this spike in login failures, to see the raw activity log. In this case, I quickly see that the majority of failures are coming from a handful of users with incorrect cache passwords.
The Top Active Users widget identifies at a glance where the majority of user activity is originating. The color coding indicates the type of activity. I can quickly filter out certain activity, like authentications or logons, if I don't want to see them, since they're high volume and can obscure other actions. I can also exclude accounts from the graph if their activity is legitimate. In this case, I want to exclude a couple of the top accounts, since they're a service account and a system account whose activity I expect.
Again, clicking on any graph element immediately takes me to the events that are behind it. Finally, across the middle of the dashboard, we have My Favorite Searches, which is where I can pin my most used searches, whether it's a custom search I've created to detect sensitive activity in my environment or built-in security searches provided out of the box by Quest. Audit Health tells me whether there are any issues that are impacting my ability to audit user activity across my on-premises and cloud properties, for example, if my on-premises events from Change Auditor have not been configured to be shared with On Demand Audit.
Finally and most importantly, we have Critical Activity. In addition to efficiently gathering and correlating all user activity across your on-premises and Office 365 environments, one of the main values On Demand Audit provides is Quest expertise in the security and audit market. Critical Activity looks for activities that Quest recommends that you keep watch over. Behind the widget are dozens of security searches which are constantly scanning the activity logs being gathered from your environment.
When any of those searches find results, they are surfaced here. The highest severity alerts are shown first. For example, the first result here shows me that suspicious replication activity occurred in my On-Prem AD, indicating that a hacker is trying to obtain a copy of my AD database.
If this