Hello. My name is Christopher Higgins, and today I would like to talk with you about solving the admin's dilemma and ultimately improving your network security. In today's IT world, data security is huge. IT admins have to effectively secure their user space with minimal impact to productivity.
We all know the age-old adage, that a chain is only as strong as its weakest link. So with that in mind, what or who do you think is the weakest link in most networks today? It's the user. Nearly 3/4, or 73%, of all Americans have fallen victim to some type of cybercrime.
In a recent survey it was reported that 90% of businesses suffered some sort of computer hack over the previous 12 months. And 77% of these companies felt that they were successfully attacked several times over the same period.
It's a constant struggle in the IT world to restrict what users have the ability to execute and access while trying to provide them with the necessary flexibility to work in an uninterrupted fashion. Additionally, we know that not all users follow best practices when it comes to securing their machines.
Back in 2014, approximately 95% of all security incidents involved human error. One obvious approach is for the IT admins to make sure endpoint devices are as secure as possible. This means minimizing the exposures workstations and servers have to security risk from both external and internal points of origin.
From there, the admins then realize the following questions will need to be answered and addressed. How to create a least-privileged user environment without affecting user productivity. How to quickly deploy critical OS and application patches in a granular fashion.
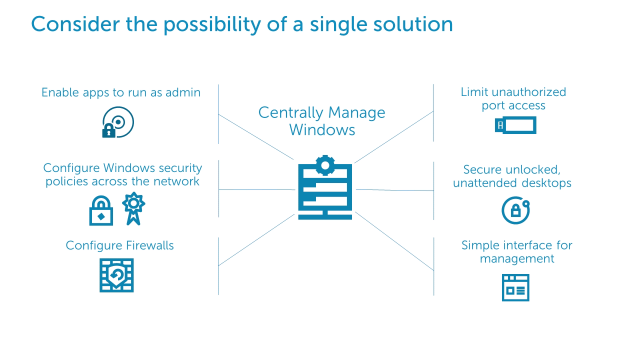
How to centrally limit unauthorized access to USB ports. How to configure Windows security policies across an entire network. How to secure unlocked desktops when left unattended. And how to centrally configure computer firewalls for maximum network security.
Managing desktop security has always been a struggle for administrators. A common, but inefficient, strategy has been to utilize a combination of different unintegrated tools, some of which can be very costly to implement from both a time and monetary standpoint. Often, IT admins also attempt to tackle security issues by severely restricting their users' access, to the point where it serves as a constant source of disruption to both the IT staff and users.
Over time, there has been a succession of solutions designed to manage the user's desktop computer. But few focus on managing the user's working environment. Often how to manage the user's experience post log in is an afterthought.
There are also many solutions to manage a user's desktop built into the operating system, namely group policies and support for various types of scripting. While effective, they are difficult to master, cumbersome to maintain, and often inflexible in application.
Now consider the possibility of a single solution. This solution would centrally limit unauthorized access to USB ports, automatically secure unlocked desktops when left unattended, provide a user-friendly, policy-based engine, allowing unique configurations for different users, groups, departments, sites, etc., configure Windows security policies across your network, centrally configure computer firewalls for maximum network security, and enable applications that require administrative privileges to be run without granting admin rights to the application user.
Many admins today are so busy building monuments of inefficiencies that they have no time to explore better, more cost-effective solutions. However, other admins make the time to save time, eventually finding a way to work smarter, not harder. Which admin can do you belong to?
Interested in a single solution which solves the admin's dilemma? Discover the Desktop Authority Management Suite, including videos, screenshot tours, detailed specification, and customer case studies. Here are some helpful links, which will get you started on your journey towards better network security through a single, simple, effective, and affordable solution.
 04:16
04:16
