In this demo, we're going to take a look at GPOADmin containers. A container allows the administrator to assign very specific tasks to individual users who are responsible for managing GPOs. To create a container, we go to the version control root. You right mouse click. And we can create a new container. We can also create subcontainers. Within each container, we will also register objects. Those objects will then be managed by the users who have permissions on those containers.
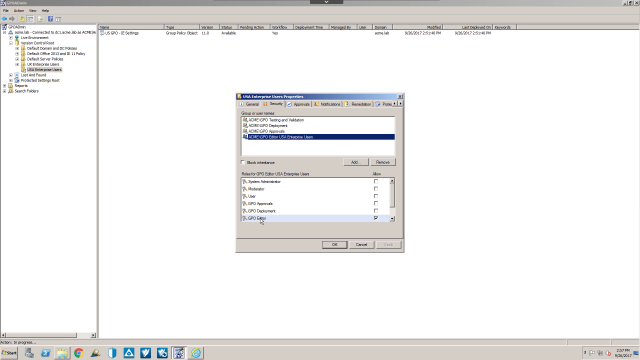
If I take a look at the US Enterprise Users container, it has one GPO in it. We can right mouse click on the container and look at the properties. On the Security tab, it shows the different roles that have been assigned to our different groups. For example, I have a user that has a GPO editor for the US Enterprise Users. And this group has been assigned the role GPO editor.
I also have some other roles, for example, a group who is allowed to test and validate the GPO. For example, they would be able to export out the GPO and import it into a test environment for testing. I also have a group that can approve the GPOs and another group that's responsible for scheduling the deployment of a GPO once it's gone through its workflow process. While GPOADmin has built-in roles, you're also able to create custom rules. So at this point, let's switch over to a workstation and take a look at what one of our GPO administrators is able to see and do.
So I've logged into a workstation as Team Era. Team Era has the ability to edit GPOs. Notice that this particular user does not see all of the other version control routes. He does not see the live environment. He only sees the US Enterprise Users container where this person is allowed to edit the GPO. I can right mouse click. Notice I have the option to check out and also edit.
If I click Edit, it will automatically be checked out and we'll go to the edit process. But we'll walk through this step-by-step. I put in a comment for why I'm checking this particular GPO out. Notice the status is checked out. I can now edit the GPO.
At this point, we need to check the GPO in. And next we can request approval. This needs to be done before the GPO is deployed.
At this point it's pending approval by our administrator.
The administrator will then receive an email to approve the GPO. Once the GPO is approved, we will see the GPO pending deployment. At this point, we can go no farther with this particular user. This user does not have the permissions to deploy. So we'll need to log in as a user that has this particular right.
So we've logged in as another user, A Grande, who has the permissions to deploy GPOs. If we take a look at the GPO that's been modified and approved, we can right mouse click. And notice that we have the deploy option available. A Grande does not have the rights to edit the GPO, to check out, to approve. The only permissions that we gave this particular user is deploy.
We click deploy. We can deploy this immediately, or we can schedule it for a later time.
So to summarize, containers in GPOADmin allow administrators to assign very granular permissions to users that are managing GPOs. Permissions can be assigned to a container, a subcontainer, and they can also be applied to the GPO objects themselves.
 05:07
05:07
